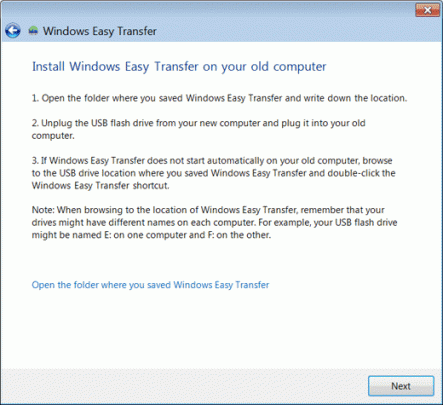
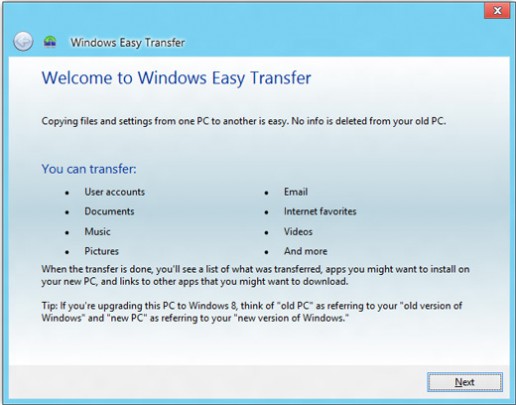
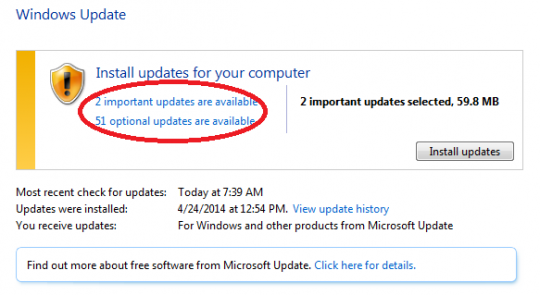
Did you just buy a new Windows laptop or desktop computer? You will probably want to bring all of your files with you too. With Windows Easy Transfer, you can transfer Windows files and settings from one Windows operating system to another.
Note that Windows Easy Transfer will not transfer files from a 64-bit version of Windows to a 32-bit version.
Also, you must open this program with an administrator account.
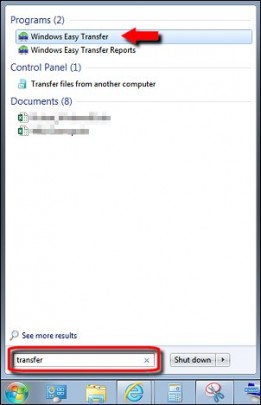
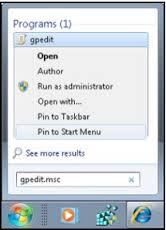
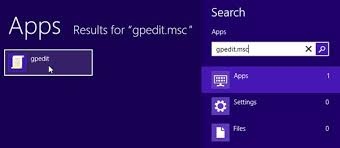
To open Windows Easy Transfer, click the Start button on your old computer and type Easy Transfer in the search box. In the list of results, click Windows Easy Transfer.
To transfer files and settings from Windows XP to 7, please refer to the following article.
If prompted for an administrator password or confirmation, enter the password or confirm the launch of the program.
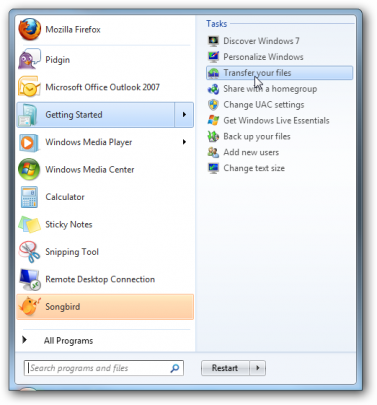
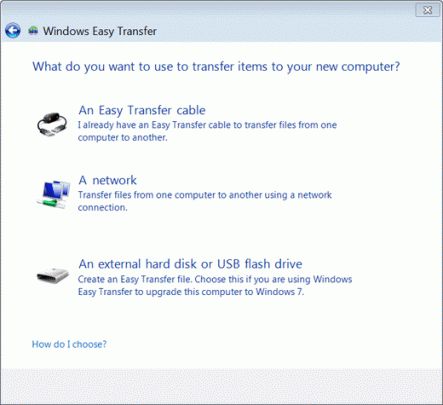
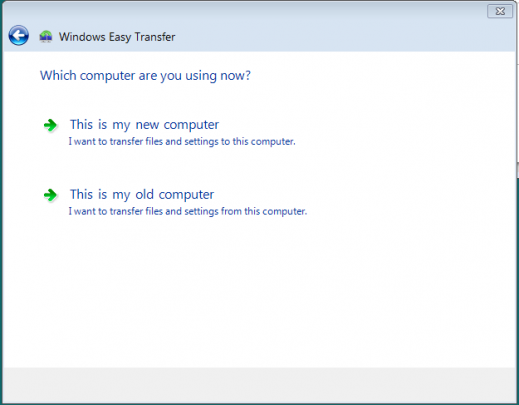
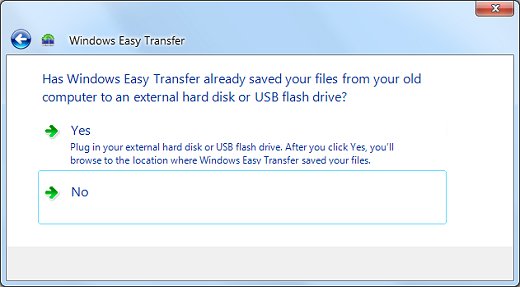
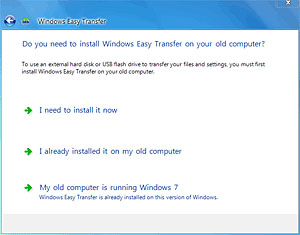
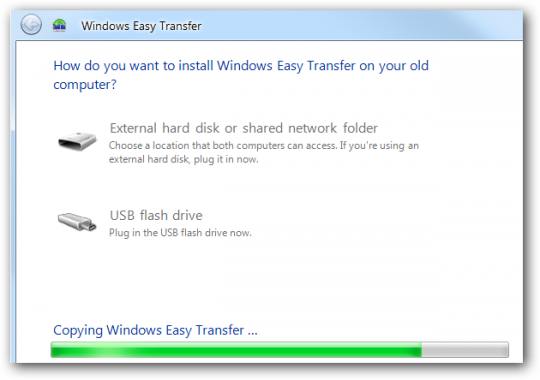
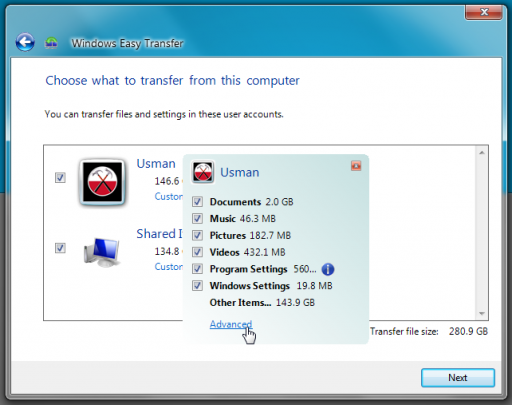
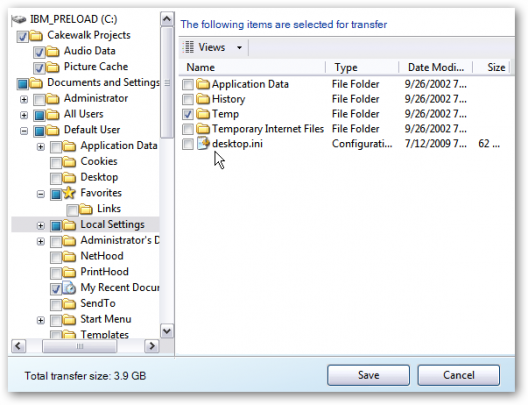
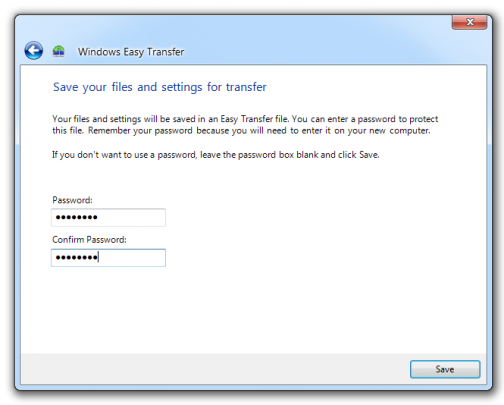
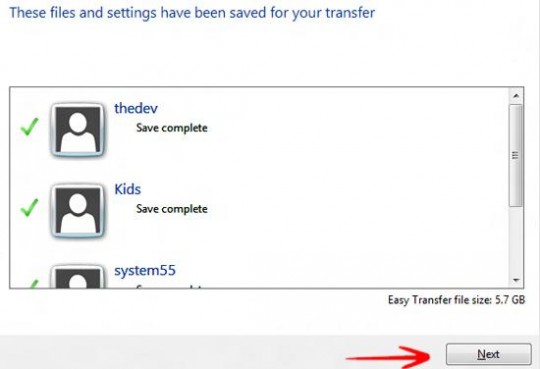
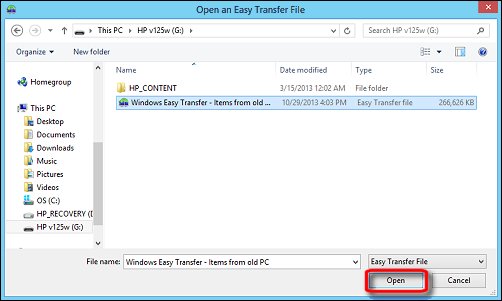
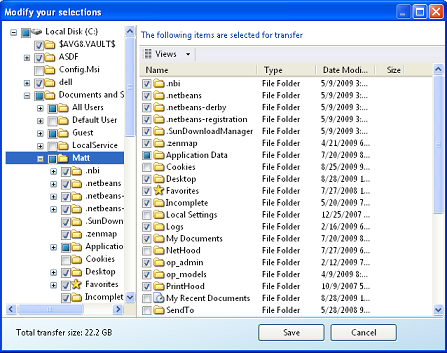
When the wizard opens, follow the step by step instructions to transfer your files. Then perform the same steps on your new computer.
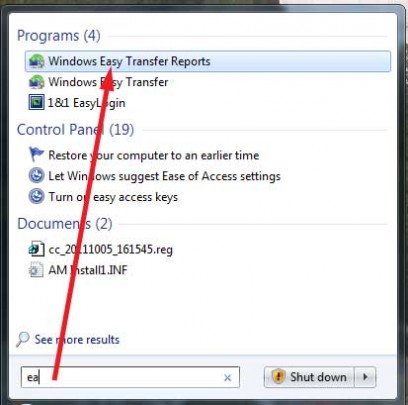
To view a report of the transfer, click the Start button, type Easy Transfer Reports. In the list of results, click Windows Easy Transfer Reports.
If prompted for an administrator password or confirmation, provide the password or issue the confirmation.
If you are moving files from a windows system to a non windows system such as Linux, Mac or Chrome, you will want to copy all of the files in your C:\Users\<username> directory using an external drive or by copying it over the network.
For more information please consult your local IT professional.
Read More