Phishing emails represent a huge risk to your business’ data security, so it’s crucial that you can identify the unmistakable signs of a phishing email.
Phishing emails represent a huge risk to your business’ data security, so it’s crucial that you can identify the unmistakable signs of a phishing email.
Data released by the Anti-Phishing Working Group has revealed a huge spike in phishing websites of 250% in Q1 2016. This represents a concerted effort by hackers to target unsuspecting computer users through a relatively old method of cyber-crime.
However, you don’t have to fall foul of the hackers’ attempts to extract sensitive data out of you. And if you follow my 5 ways to spot a phishing email you should be safer than ever!
1. Asks for Personal Information
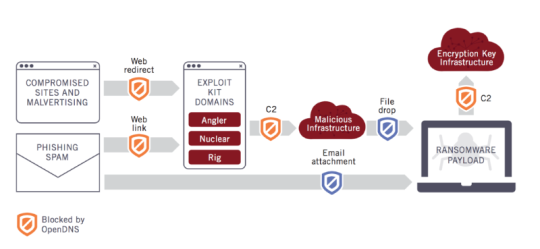
A legitimate email will never ask you to disclose personal information, but a phishing email will, literally, be fishing for this information. For example, your bank will never email you and request your online banking details for ‘verification’ purposes.
Your bank wouldn’t need to verify this as they would already have the definitive details on their database, but you would be surprised by how many people fall for this scam.
2. Spelling Mistakes
Big brands take their marketing very seriously, so any emails released by them will have been crafted by people who know how to write. And, more importantly, they’ll know how to spell!
Hackers, on the other hand, aren’t well known for their dedication to spelling and grammar. That’s why their phishing emails are littered with spelling mistakes. If you pick up on at least one spelling mistake, then that’s enough to start treading carefully.
3. Mismatched Links
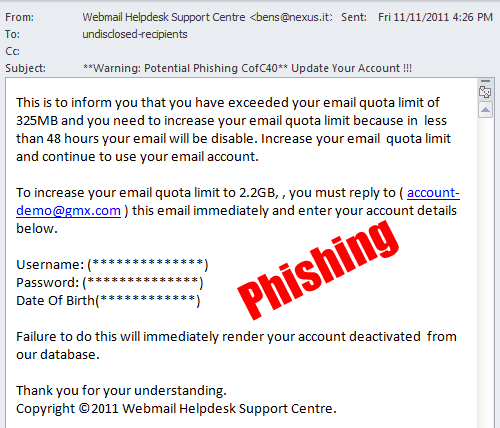
In order to drive you towards phishing websites (which can install malware and steal data from you), hackers need to trick you into clicking their links. Now, a quirk of web design is that your link can say something like bankofamerica.com but the coding behind this link will actually send you somewhere else.
And the best way to test a link is to simply hover your mouse cursor over the link, a small preview window of the actual link will then appear and you can judge whether this is genuine or not.
4. Misleading Display Names

Phishing emails attempt to gain your trust by spoofing the sender’s display name, so you need to be vigilant that you don’t take this at face value. Many pieces of email software will, by default, only show the sender’s display name in your inbox.
And this display name can be changed to anything the hacker wants. For example, if you receive an email which has a display name of ‘Microsoft Security Team’ it doesn’t mean the email has actually been sent by the Microsoft Security Team!
When you look a little closer at the email, you’ll discover that the email address it has been sent from isn’t a genuine Microsoft one, so it’s time to delete that email!
5. Threatening Content
Many hackers hope to intimidate email recipients in order to deceive them into clicking their links or downloading their attachments. It may be that they claim they’re from a government agency such as the FBI and that they’re accusing you of illegal activity.
With this fear in mind, many users feel as though they have to comply with the email’s demands, especially when it’s accompanied by official logos and signatures. However, no matter what you think of the government, they are not going to send you threatening emails which demand money, so please feel confident in deleting these!
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More