
A Zero-day Microsoft Windows Exploit CVE-2014-4114 has been found which impacts all versions of Windows. Here’s what you need to know to protect yourself.
The Russian espionage group, known as the “Sandworm team”, are the prime suspects believed to have launched a campaign to exploit a range of Microsoft Windows vulnerabilities. The exploits are classified as Zero-Day, meaning they are so new that no anti-virus companies have figured out how to detect them yet. The ultimate goal is to inject and execute malicious code into systems and networks to leach data from computers.
Their targets have involved NATO, US academic organizations, Western European Union and Ukrainian government agencies, European energy and telecommunication companies.
Systems are infected from files being attached to legitimate looking emails and extended through to social engineering methods. Most versions of Windows are affected – including server 2008 and 20012, but excluding Windows XP.
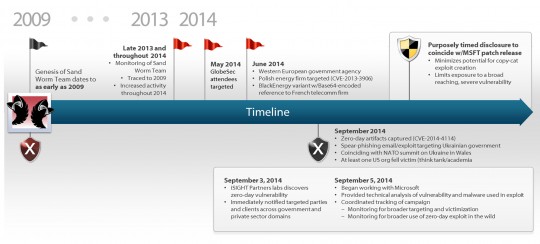
iSight has provided a timeline of the Sandworm infection campaign.
The cyber intelligence firm, ISight, has been monitoring Sandworm’s activities. After alerting Microsoft, a patch was released called MS14-060 which is found in Window’s Automatic Updates. The fix is still an on-going work in progress.
The vulnerability explained
Here is a high level overview of what the CVE-2014-4114 Zero Day exploit entails:
- The vulnerability allows a computer to have code executed remotely through a file that is initially opened by an unsuspecting user via an email attachment.
- Within most software installation files, you’ll find a component called OLE (Object linking and Embedding) Package Manager.
- An OLE package allows applications to share files and functionality.
- The OLE package manager contains a file which permits it to download and run INF files.
- This is where a computer is vulnerable since a hacker can run any program, virus or malware on a system.
- Any acquired arbitrary code can then run from the downloaded INF files, which is presumed by the system to be associated with the application’s package.
- This package will run from the logged-in user’s credentials, such as an administrator or anyone with admin rights.
- The danger then rests from specific commands given to the file during the execution of the application.
- It has been observed that unsuccessful attempts from this exploit can also lead to a denial of service, which can lead to service disruption.
- As mentioned previously, the usual mode of target is through fake emails with attachments and social engineering, where the user would need to be convinced and tricked into opening the file.
Proactive measures to prevent an infection
Follow these guidelines to protect yourself or to quickly recover from a compromised system.
- Install the latest operating system updates
- Do not open any unknown files in the work place or at home, especially those received through email, shared through websites or any other sources, such as social media sites
- If you are asked to click on an unknown file, always question it, no matter who it may be
- Check and update your anti-virus at least daily
If you find your system compromised
- Inform your IT support asap.
- Take your computer off the network to isolate it
- Run a virus scan until all infections are removed
- Lock down the admin privileges and allow only admin users who need it for their job role
- Optionally reconfigure firewall ports and lock out any vulnerable ones that are open and not essential
For more details about the Zero-day Microsoft Windows Vulnerability CVE-2014-4114 issue and other security issues putting your business and private data at risk, contact your local IT professionals.
Read More




