

We all rely on tech support at some point during our working week, but hackers are now using this as a front to scam businesses out of thousands of dollars.
It’s a scam which is becoming so widespread that the FBI have stepped up and announced that, in the last three months, close to two and a quarter million dollars have been stolen from businesses. These losses are the result of just over 3,500 separate incidents, so they can’t be dismissed as isolated incidents.
The actual scam involves hackers impersonating tech support teams and taking control of users’ PCs, so this is a very deceitful scam and one which we need to investigate.
Understanding the Scam
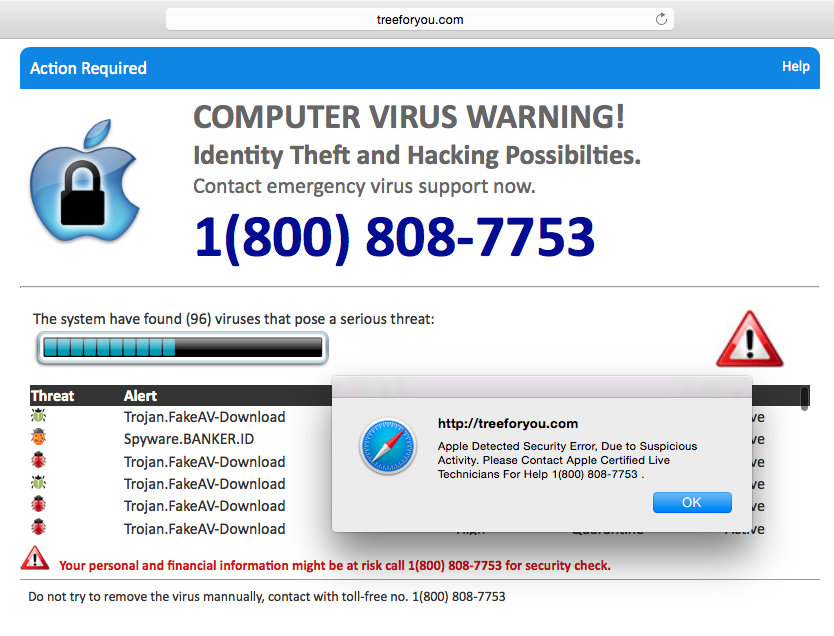
This latest attempt at swindling businesses out of money is a particularly clever one as it preys on the anxiety of computer users. Those affected find that they will receive one of the following prompts which all demand handing over remote access:
- A pop up message which states that viruses have been detected on the PC and that it’s under attack. A ‘helpful’ phone number is then provided for that individual to contact technical support.
- A telephone call from a tech support employee – usually with a foreign accent – who claims to have evidence that the PC is infected and sending out error messages. This tech support employee will claim that they can help resolve the attack.
- A ‘Blue Screen of Death’ will be displayed which warns that the PC has become infected and that the PC user needs to contact a technical support number.
All these methods lead to direct communication with a shady individual who will request that any mobile devices are connected to a PC to carry out detailed security scan. Naturally, these ‘scans’ always reveal numerous viruses and a fee is then demanded to eradicate these viruses.
Resisting the Tech Support Scam
 As you can see, from the amount of money stolen so far, this is a very serious scam, so you need to make sure that your employees know what to do if they’re affected. Therefore, you need to communicate the following advice:
As you can see, from the amount of money stolen so far, this is a very serious scam, so you need to make sure that your employees know what to do if they’re affected. Therefore, you need to communicate the following advice:
- Make sure that all security software is up to date. There have been some reports that security software has given alerts just before these scams have been attempted online.
- Once one of the suspicious pop up messages or Blue Screens of Death are received, the user should shut down their device straight away. This will usually clear the intrusive demands for action.
- The hackers will try and instill a sense of fear and urgency to scare users into making quick payments, so users must remain calm and disconnect the call.
- Users must avoid giving over any remote access to unauthorized individuals who are posing as tech support employees. Reputable tech support teams will never demand this sort of access.
Final Thoughts
It’s important that PC users are aware that hacking doesn’t always involve downloading malicious software. Sometimes, the age old act of deception can be employed to create a sense of fear which leads to people making snap decisions and losing money as a result.
If you have been affected by this particular scam then you should report it at www.ic3.gov
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More








 Thankfully, your money is pretty safe within a bank. Even if they do suffer any losses through cyber-crime, it will be the bank who takes the hit and not your personal account. However, it does raise some interesting questions about security.
Thankfully, your money is pretty safe within a bank. Even if they do suffer any losses through cyber-crime, it will be the bank who takes the hit and not your personal account. However, it does raise some interesting questions about security.
 Adobe has suffered another embarrassing attack which exploits their Flash software and this time the malware has been hidden in an Office document.
Adobe has suffered another embarrassing attack which exploits their Flash software and this time the malware has been hidden in an Office document.


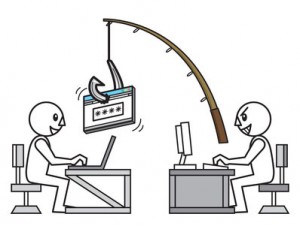 Phishing is the process of stealing personal information (login details, credit card details etc) from consumers through the following methods:
Phishing is the process of stealing personal information (login details, credit card details etc) from consumers through the following methods: