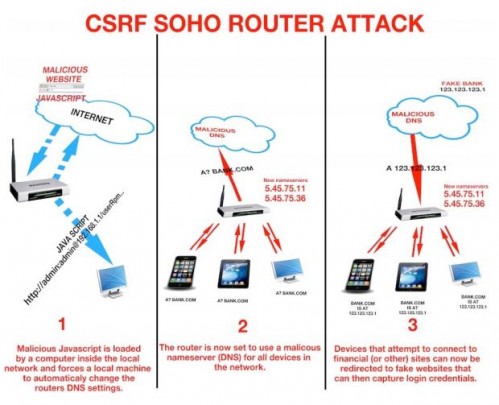
A major bug has been found in the popular OpenSSL library used by thousands of online merchants, email providers and banks. The bug allows anyone on the internet to read a user’s private information while it is being sent back and forth to the website. A security advisory has been issued by OpenSSL.
Why is the bug called Heartbleed?
The code affected by this bug is in the heartbeat portion of the protocol which keeps the connection to the website active. When the bug is exploited it causes memory to leak its content while it is being sent over the internet, which contains sensitive and private information.
How does this affect me?
If the website you are logging in to, such as your bank, email or an online store uses a version of OpenSSL that has this bug:
- An attacker can open a connection to your bank over and silently download among other things the keys used to prove the bank is who they say they are.
- They can then pretend to be your bank and you will not notice anything different, while all of your communication is being stolen.
It is estimated that up to 70% of internet websites are affected by this bug. Companies can fix the bug by upgrading to the latest version of OpenSSL, creating new certificates and removing old certificates.
How can I protect myself?
First check if the website you are accessing has an “https” in front of the address, meaning it should be a secure connection. All banks, email webpages and online stores should have this:
If it is a secure connection, enter the website here to check if the bug exists.
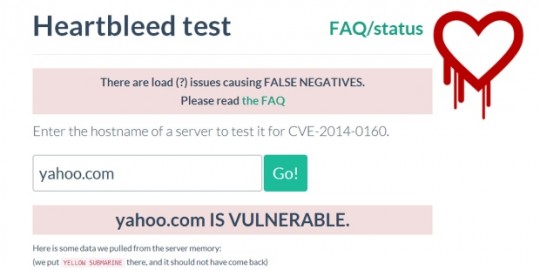
http://filippo.io/Heartbleed/ will let you know if the site has the Heartbleed Bug.
If it does exist, avoid using the website until they have upgraded their OpenSSL. For further assistance with the Heartbleed bug or other security issues, contact your local IT professionals.
Read More