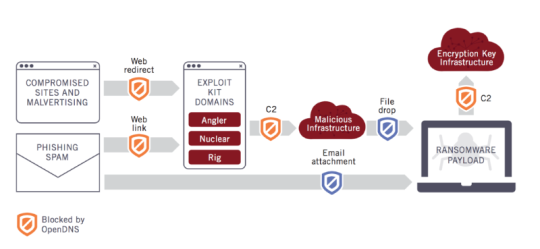
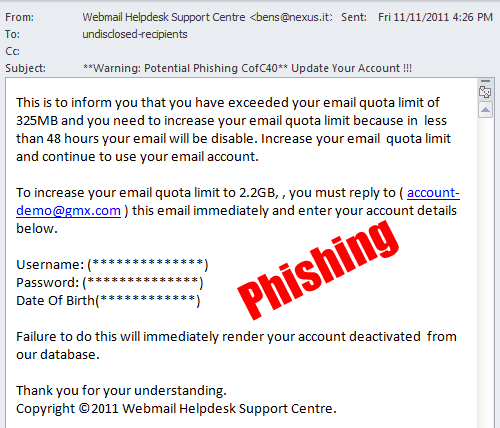
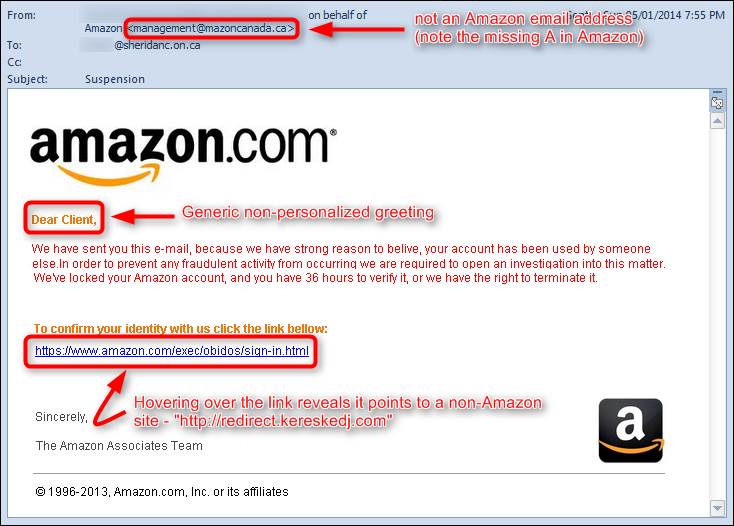
Anyone who sets foot online these days is at risk of falling victim to hackers, so it’s a good idea to know when you’ve been hacked.
After all, the sooner you realize you’ve been hacked, the sooner you can start working to remove the infection from your PC and make your data secure again. However, hackers are stealthy individuals and you may have to look a little closer than usual to catch them in the act.
And, to give you a helping hand, here are 7 tell-tale signs that you’ve been hacked.
1. Slow Internet Connection
If you internet connection has ground to a halt then this could indicate that you’ve been hacked. Due to an increase in network activity – caused by hackers using your bandwidth to commit malicious activity – this can render your normal internet access next to useless.
2. Unusual Access Times

It’s always a good idea to keep an eye on the times at which your network is accessed by new connections. In general, access during your normal working hours is to be expected, but new connections outside these times should be treated as suspicious. Hackers, you see, are likely to use automated software that is active throughout the entire day rather than between 9-5.
3. Disabled Antivirus
There are very few occasions that you would deliberately disable your antivirus, so if you notice that your antivirus software has been disabled this should start ringing alarm bells. And, for a hacker, if they’re able to disable your antivirus software, this allows them free rein to download all sorts of malware to your PC.
4. Unable to Log on?
One of the first things a hacker will try to alter on your system is your login credentials as this restricts your access and gives them more time to cause trouble. Therefore, if you’re absolutely sure that you’re entering the correct username/password combination, you need to consider that you may have been hacked.
5. Strange Cursor Movements
Due to hardware and software issues, your mouse may occasionally move without any user interaction. However, these are usually haphazard movements and certainly don’t double click on programs to open them. If you ever see your mouse ‘come to life’ on its own then it’s time to shut your PC down and call in the experts!
6. Fake Antivirus Messages
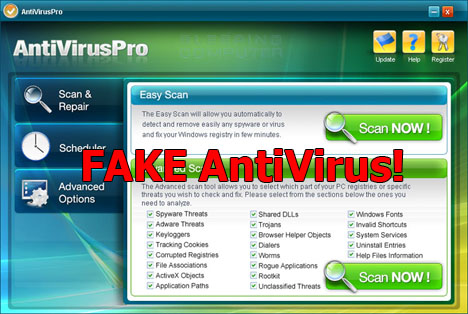
You should always make sure that your network users are aware of the antivirus software that you’re running; this is because one way that hackers can target your PCs is through fake antivirus messages. These will usually advise users that a virus scan has been run and viruses detected that only this piece of software can remove. And this will involve being redirected to a website to download the “antivirus software”, but in reality you’ll be downloading nothing but malware.
7. Internet Searches Redirected
Hackers are keen to disrupt your activity for their own benefits and one way to do this is to redirect your internet searches to alternate websites. So, if you find your internet searches suddenly start taking you to dubious websites then there’s a good chance you’ve been hacked.
For more ways to secure and optimize your business technology, contact your local IT professionals.
Read More