Ever needed to share computer instructions or steps with another person? Maybe you’re the only person in the office that knows the special Excel formula trick. The Problem Steps Recorder allows you to record the steps you took to complete a Windows task for future reference or to share it with others.
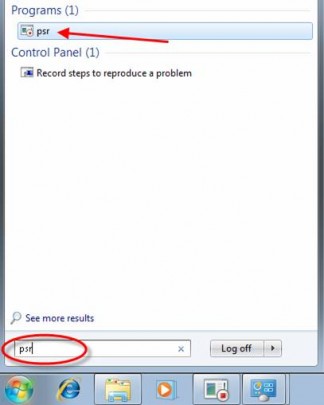
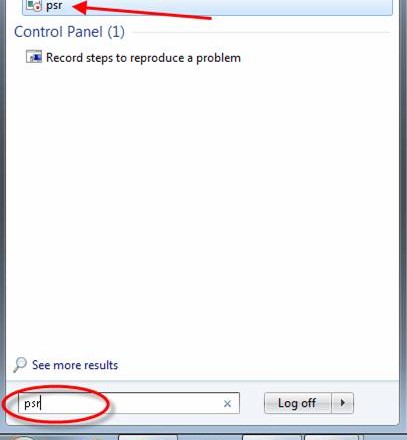
To open the PSR (Problem Steps Recorder), click the Start button and type ‘psr’ in the search box. On the list of results, click ‘psr’.
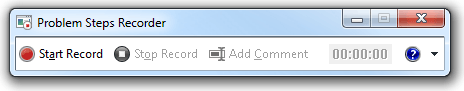
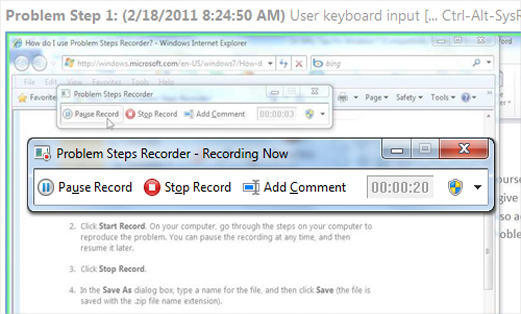
When performing a Windows task whose steps you want to save, click ‘Start Record’ on the ‘Problem Steps Recorder’ console. The PSR has a pause button you can click to pause recording.
Click ‘Stop Record’ to finish recording. In the ‘Save As’ dialog box, save the recording as a zip file to a desired location.
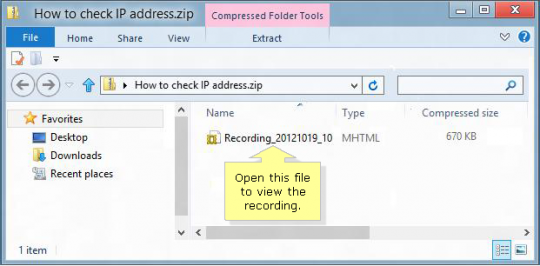
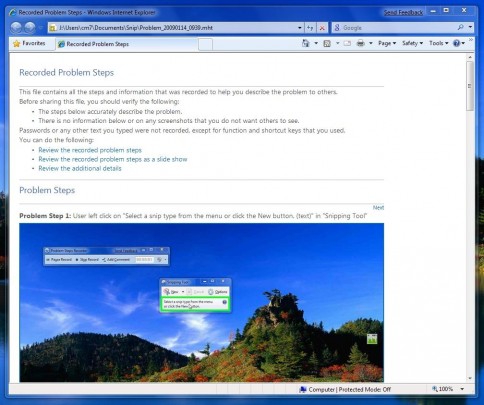
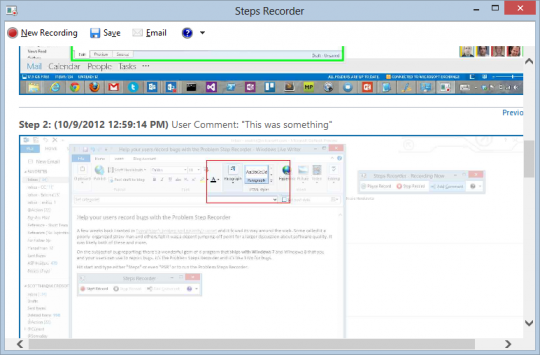
To view the recording, open the zip file by double clicking it. Next, double click the recording, which will open in the default web browser.
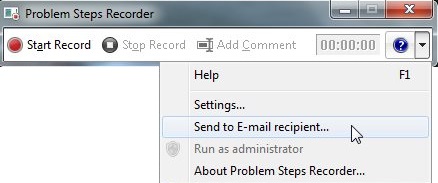
The saved zip file containing the recording can be sent by email by clicking the help down arrow and by selecting ‘Send to E- mail recipient’.
The default email client will open with the last recorded file attached to it.
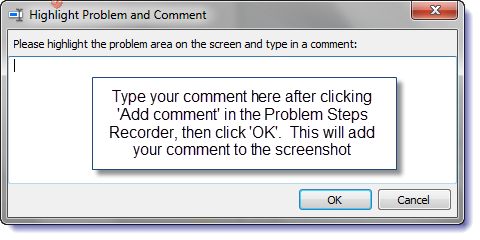
Please note that the file must be saved first. The steps of a problem can be annotated by clicking the ‘Add Comment’ button.
Use the mouse to highlight the part of the screen you want to comment on.
Type in the ‘Highlight Problem and Comment’ box, and click ‘OK’.
For more tips and tricks on your PC, contact your local IT professionals.
Read More