TP-Link is among the vendors affected by the SOHO pharming campaign.
Recently, it was discovered that several hundred thousand routers fell victim to a hijacking scheme that could become a prevalent problem to many internet users worldwide. The attack, dubbed as a ‘small office/home office (SOHO) pharming campaign,’ was targeting Vietnam, but according to a report by Team Cymru, the SOHO pharming campaign also made its way into regions like the US and Italy.
The criminals behind the pharming campaign took advantage of exploitable security holes in various consumer-grade routers, and from there they were able to redirect users to malicious websites to steal login credentials and/or dropped malware onto the users’ computer. The scary part about this SOHO campaign is that more than one type of routers are affected. According to Team Cymru, the compromised routers could be a brand name like D-Link or and off-brand like TP-Link.
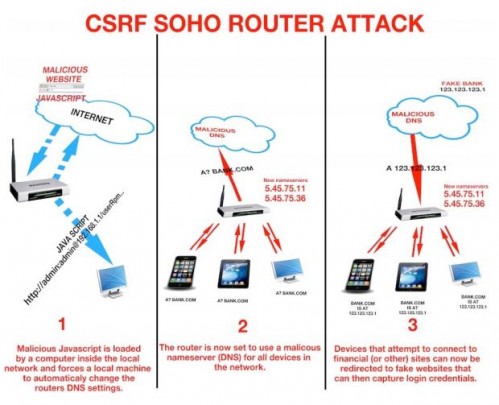
A diagram depicting the ‘man-in-the-middle’ hijacking scheme from Team Cymru.
Cyber security experts found that once the attackers had control of their targeted routers, they changed the devices’ Domain Name System (DNS) settings to force users to send out requests to the 5.45.75.11 and 5.45.75.36 IP addresses. The new DNS settings then acts as a ‘middle-man’ and redirect users to malicious sites instead of legitimate ones.
While it is easy to point the fingers directly at the people manufacturing the routers, it’s not completely their fault. There’s no such thing as a ‘hands-off’ policy when it comes to protecting yourself from intrusions by cyber criminals. That said, there are a few things many router owners can do to lessen their chances of becoming victims to the router hijacking scheme.
- Disable router’s remote user-mode and graphical user interface. Disabling remote access will help keep users who aren’t directly connected to your network from accessing your routers’ admin properties. Disabling the GUI will, reportedly, mitigate the likelihood that someone can find a hole in the routers’ software. Instead of making changes to the routers’ setting via a graphical interface, try to change the settings via command lines.
- Corporate networks may want deploy tracking systems (i.e. an HTML code on the externally facing servers) to detect possibly malicious IP addresses.
- All SOHO router settings (especially DNS) should be controlled at the host level.
- Admins must proactively monitor router settings periodically to ensure that the router’s DNS is pointing at those that belong to their internet service providers (ISP).
These are just a few of the basic security measures you must consider if you or your organization is using a SOHO router. Should you have any questions or concerns regarding the recent SOHO pharming campaign or what you should do tighten up your network security, contact our IT professionals.
Read More